See new link here..
Managed Service Identity (MSI) for Azure resources
https://docs.microsoft.com/en-us/azure/active-directory/msi-overview
| Managed Service Identity (MSI) is currently a preview feature of Azure Active Directory and is for evaluation purposes only. MSI is deploying to regions globally and may take time to appear in your region. Make sure you review the known issues before you begin. For more information about previews, see Supplemental Terms of Use for Microsoft Azure Previews. |
A common challenge when building cloud applications is how to manage the credentials that need to be in your code for authenticating to cloud services. Keeping these credentials secure is an important task. Ideally, they never appear on developer workstations or get checked into source control. Azure Key Vault provides a way to securely store credentials and other keys and secrets, but your code needs to authenticate to Key Vault to retrieve them. Managed Service Identity (MSI) makes solving this problem simpler by giving Azure services an automatically managed identity in Azure Active Directory (Azure AD). You can use this identity to authenticate to any service that supports Azure AD authentication, including Key Vault, without having any credentials in your code.+
How does it work?
When you enable Managed Service Identity on an Azure service, Azure automatically creates an identity for the service instance in the Azure AD tenant used by your Azure subscription. Under the covers, Azure provisions the credentials for the identity onto the service instance. Your code can then make a local request to get access tokens for services that support Azure AD authentication. Azure takes care of rolling the credentials used by the service instance. If the service instance is deleted, Azure automatically cleans up the credentials and the identity in Azure AD.+
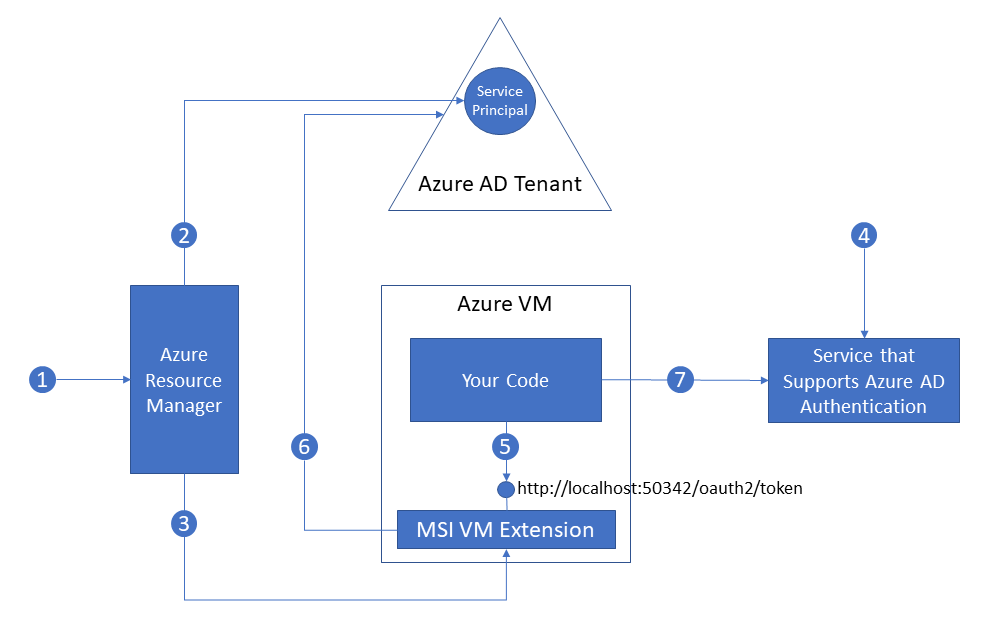
Here’s an example of how Managed Service Identity works with Azure Virtual Machines.+
-
- Azure Resource Manager receives a message to enable MSI on a VM.
- Azure Resource Manager creates a Service Principal in Azure AD to represent the identity of the VM. The Service Principal is created in the Azure AD tenant that is trusted by this subscription.
- Azure Resource Manager configures the Service Principal details in the MSI VM Extension of the VM. This step includes configuring client ID and certificate used by the extension to get access tokens from Azure AD.
- Now that the Service Principal identity of the VM is known, it can be granted access to Azure resources. For example, if your code needs to call Azure Resource Manager, then you would assign the VM’s Service Principal the appropriate role using Role-Based Access Control (RBAC) in Azure AD. If your code needs to call Key Vault, then you would grant your code access to the specific secret or key in Key Vault.
- Your code running on the VM requests a token from a local endpoint that is hosted by the MSI VM extension: http://localhost:50342/oauth2/token. The resource parameter specifies the service to which the token will be sent. For example, if you want your code to authenticate to Azure Resource Manager, you would use resource=https://management.azure.com/.
- The MSI VM Extension uses its configured client ID and certificate to request an access token from Azure AD. Azure AD returns a JSON Web Token (JWT) access token.
- Your code sends the access token on a call to a service that supports Azure AD authentication.
Each Azure service that supports Managed Service Identity will have its own method for your code to obtain an access token. Check out the tutorials for each service to find out the specific method to get a token.+
Which Azure services support Managed Service Identity?
Azure services that support Managed Service Identity can use MSI to authenticate to services that support Azure AD authentication. We are in the process of integrating MSI and Azure AD authentication across Azure. Check back often for updates.+
Azure services that support Managed Service Identity
The following Azure services support Managed Service Identity.+
| Service | Status | Date |
|---|---|---|
| Azure Virtual Machines | Preview | September 2017 |
| Azure App Service | Preview | September 2017 |
| Azure Functions | Preview | September 2017 |
Azure services that support Azure AD authentication
The following services support Azure AD authentication and have been tested with client services that use Managed Service Identity.+
| Service | Resource ID | Status | Date |
|---|---|---|---|
| Azure Resource Manager | https://management.azure.com/ | Available | September 2017 |
| Azure Key Vault | https://vault.azure.net/ | Available | September 2017 |
| Azure Data Lake | https://datalake.azure.net/ | Available | September 2017 |
How much does Managed Service Identity cost?
Managed Service Identity comes with Azure Active Directory Free, which is the default for Azure subscriptions. There is no additional cost for Managed Service Identity.+
Support and feedback
We would love to hear from you!+
-
- Ask how-to questions on Stack Overflow with the tag azure-msi.
- Make feature requests or give feedback on the Azure AD feedback forum for developers.
Try Managed Service Identity
Try a Managed Service Identity tutorial to learn end-to-end scenarios for accessing different Azure resources:+
If you just want to learn the basics of enabling MSI on an Azure resource :+
| For Azure resource | Enable/remove MSI using |
|---|---|
| Azure VM (Windows) | The Azure portal |
| PowerShell | |
| Azure CLI | |
| Azure Resource Manager templates |
Then learn how to use Role Based Access Control (RBAC) to give an MSI permission to access another Azure resource :+
| From MSI-enabled resource | Assign access to another Azure resource using |
|---|---|
| Azure VM (Windows) | The Azure portal |
| PowerShell | |
| Azure CLI |
IGNORE BELOW
Original Link
Posted on September 14, 2017
A common challenge in cloud development is managing the credentials used to authenticate to cloud services. Today, I am happy to announce the Azure Active Directory Managed Service Identity (MSI) preview. MSI gives your code an automatically managed identity for authenticating to Azure services, so that you can keep credentials out of your code.
What is Managed Service Identity and how do I use it?
Your code needs credentials to authenticate to cloud services, but you want to limit the visibility of those credentials as much as possible. Ideally, they never appear on a developer’s workstation or get checked-in to source control. Azure Key Vault can store credentials securely so they aren’t in your code, but to retrieve them you need to authenticate to Azure Key Vault. To authenticate to Key Vault, you need a credential! A classic bootstrap problem. Through the magic of Azure and Azure AD, MSI provides a “bootstrap identity” that makes it much simpler to get things started.
Here’s how it works! When you enable MSI for an Azure service such as Virtual Machines, App Service, or Functions, Azure creates a Service Principal for the instance of the service in Azure AD, and injects the credentials (client ID and certificate) for the Service Principal into the instance of the service. Next,
- Your code calls a local MSI endpoint to get an access token
- MSI uses the locally injected credentials to get an access token from Azure AD
- Your code uses this access token to authenticate to an Azure service
And that’s it! The access token can be used directly with a service that supports Azure AD authentication, such as Azure Resource Manager. If you need to authenticate to a service that doesn’t natively support Azure AD, you can use the token to authenticate to Key Vault and retrieve credentials from there. Azure and Azure AD take care of rolling the Service Principal’s credentials. Your code and your developers will never see or manage them.
Try it
Today we are announcing previews of Managed Service Identity for:
Click the links to try a tutorial!
Managed Service Identity is a feature of Azure AD Free, which comes with every Azure subscription. There is no additional charge for using Managed Service Identity.
We would love to hear from you! You can ask how-to questions on Stack Overflow using the tag “azure-msi”, or post feature feedback or suggestions to the Azure AD developer feedback forum