Alex Simons (AZURE) Microsoft
Getting started
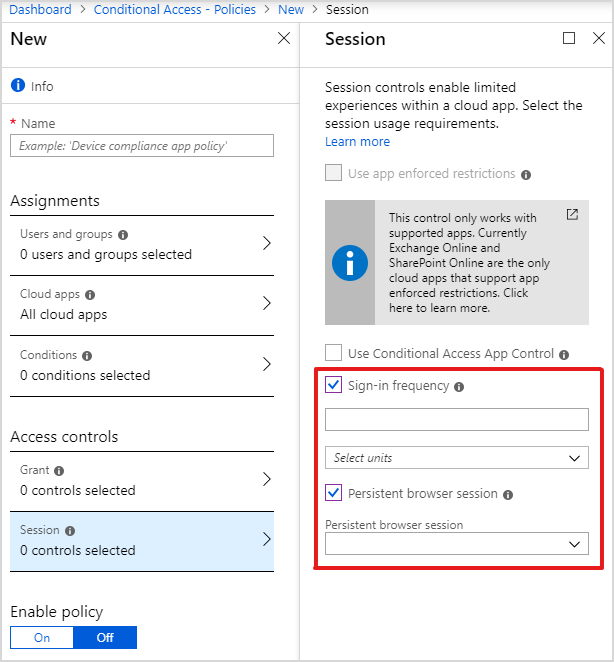
To get started, set the sign-in frequency, which defines the time period before a user is asked to sign-in again when attempting to access a resource. You can set the value from 1 hour to 365 days.
You can also set a persistent browser session. This allows users to remain signed in after closing and reopening their browser window. We support two new settings: always persist or never persist. In both cases, you’ll make the decision on behalf of your users and they won’t see a “Stay signed in?” prompt.
Configuring authentication sessions for your environment
Configuring how often your users need to provide credentials for sign-in and if their browser sessions will be persisted is a delicate balance between security and productivity. For most deployments, the Azure AD default configuration for authentication session already provides the necessary security while balancing a productive user experience. Asking users to frequently sign-in may not make sessions more secure and can hinder a productive user experience. So it’s important to consider if changing the default configuration is necessary for your environment.
For complex deployments, you might have a real need to restrict authentication sessions. Fine grained conditional access controls allow you to create policies that target specific use cases within your organization such as data access from unmanaged or shared devices, without affecting productivity of compliant users. With conditional access you can now adapt authentication session lifetime depending on sensitivity of a resource, user account privilege, authentication strength, device configuration, location and many other conditions.
We’re excited to provide these new enhancements to our customers and as always, we’d love to hear any feedback or suggestions you have. Let us know what you think in the comments below.
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division